The Italian hacking firm, Hacking Team, world renowned for their surveillance and hacking tools, were on Sunday 5, July 2015, served a dose of their own medicine when hackers ravaged their company digital files and uploaded over 400 GB of data consisting of emails, contracts and financial documents online for anyone willing to sacrifice the bandwidth.
The twitterverse exploded with reactions ranging from hilarity to concern.
The quality of the HackingTeam's malware code for Linux is very bad. Bad indentation, stack overflows, hard-coded paths, etc… Crap.
— Hacker Spy Network (@HackerSpyNet) July 6, 2015
Fact: #HackedTeam's arsenal included evidence planting malware. No matter how they try to spin this, the truth is already out there.
— Mário (@ticklemynausea) July 15, 2015
Some one call the police! HackingTeam sold to Sudan?! And telling hem to use a VPN?! Thats a violation of EU law… #IsHackingTeamAwakeYet
— Clicksights (@Clicksights) July 6, 2015
https://twitter.com/micahflee/status/621013391834943488
Further investigation revealed that several Nigerian individuals and governments have approached the Hacking Team firm to solicit their services at different times.
Since early July when details of the Hacking Team security leak surfaced, the plot has thickened. In case you weren’t following before now, we’ve created a summary of the curious tale. More details are coming to light as journalists comb through the leaked files, but here are the key facts that have emerged as of now.
Hacking Team are notorious “hackers for hire”
Hacking Team is an Italian company well known for its surveillance tools and hacking services. It has also gained notoriety for its “hackers for hire” stance as its activities involves helping many governments and law enforcement agencies monitor and track down internet users via ethical and unethical methods, for a fee. Maybe that’s because the tools they sell their clients can be used to attack, infect and monitor target PCs and smartphones in a stealthy way.
Please enjoy this list of @hackingteam's customers from their Wiki. Kazahkstan! Sudan! Russia! Saudi Arabia! pic.twitter.com/xdKGiRFV6f
— Eva (@evacide) July 6, 2015
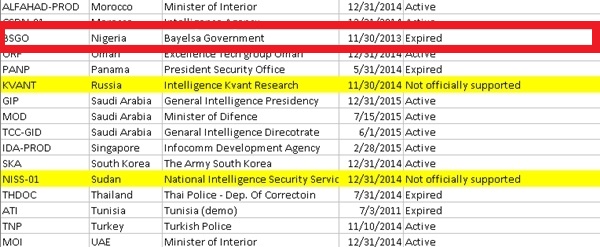
The complete list of Hacking Team’s client list was later uploaded on Pastebin. Just CTRL+F and search Nigeria or Bayelsa.
The Bayelsa State government secured Hacking Team’s services
In emails dating as far back as October 2012, it’s apparent that Bayelsa state government secured Hacking Team’s services. What they required those services for are anyone’s guess. All we know is that they are in the venerable company of other Hacking Team clients such as Uzbekistan, Russia, Kazakhstan, Saudi Arabia and the United Arab Emirates.
Somehow, they managed to do this without procuring an End User Certificate
One of the prerequisites for the purchase of international defence tools, the kind Hacking Team offers clients, is an End User Certificate. This is a document that can be issued only by the office of the National Security Adviser.
A detailed scouring of the hacked files uploaded on the internet, revealed a chain of email conversations showing that the Bayelsa state government presented Hacking Team said document. But there’s a little problem with that. The office of the National Security Adviser has denied ever issuing such the document to the Bayelsa state government.
So, how did Bayelsa state government successfully engage Hacking Team and acquire their hacking and surveillance tools?
Had the Italian hacking firm not been compromised earlier this month, this information would not have surfaced
This revelation has several implications one of which is the likelihood that the Bayelsa state government broke an EU law which prohibits the sale of surveillance tools without an End User Certificate issued by the national security authority of the client country. It also implicates the Bayelsa state government as it appears they bypassed the office of the NSA and forged an End User Certificate.
It wasn’t just Bayelsa State. Nigeria’s National Security Adviser might have tried to procure said hacking tools as well
According to a Premium Times report, one Mrs. Yemi Animashaun of Tunsmos Petroleum was reported to be the proxy that attempted to broker the transaction. Twice. Albeit unsuccessfully, for reasons that aren’t quite clear.
Former Akwa Ibom state governor, Godswill Akpabio is also reported to have shown interest in Hacking Team’s services.
Nigerians react
On the homefront, the response to the unfolding narrative has ranged from mildly angered to curiousity to humor.
Question of the day: What did the Bayelsa State government need hacking software for? http://t.co/nijNyP33LD
— Chxta (@Chxta) July 8, 2015
@ogundamisi those who aspire to leadership positions at all levels needs proper psychological evaluation
— tejumola (@tejuspoint) July 7, 2015
https://twitter.com/stalnig/status/618148987397255168
Speaking to Sahara Reporters, Mr. Iworiso-Markson, spokesperson for Bayelsa state governor, said these allegations are “absolutely untrue”.
“That is part of a series of propaganda from those who are unable to contest ideas of development with the governor,” he said.
Gbenga Sesan, Executive Director of Paradigm Initiative Nigeria, while speaking to Premium Times had this to say: “The Bayelsa hacking saga came to light a little too late, though it could point to a bigger systematic programme by the government.”
If you’d like to read all the coverage on the topic, see the following links
- Hacking Team hacked: firm sold spying tools to repressive regimes, documents claim ,, The Guardian: July 5, 2015
- Hacking Team, Bayelsa govt’s internet surveillance contractor, hacked,, Premium Times: July 6, 2015
- Bayelsa Governor hires world’s most ruthless hackers for N100M to hack computers, phones in Nigeria,, Premium TImes: July 9, 2015
- Bayelsa Governor forges End User Certificate to procure N100M hacking tools,, Premium Times: July 15, 2015