According to a report by cybersecurity firm Unit 42, South Africa based hacker group “Automated Libra” is behind an elaborate crypto mining scheme referred to as “ PurpleUrchin”, which has cost major cloud providers, including Microsoft and Salesforce, millions of dollars in resources and unpaid bills.
Freejacking works by using free (or limited-time) cloud resources to perform crypto mining operations. Automated Libra’s scheme fraudulently used the cloud platforms’ resources to perform crypto mining operations then traded the mined cryptocurrencies.
Play and run tactics
According to Unit 42’s report, beyond exploiting the free trials, Automated Libra also employed what is referred to as a “play and run” tactic whereby the actors used cloud resources from the likes of Microsoft and Salesforce for the crypto mining operations without paying the requisite fees.
The group did this by creating and using fake accounts using falsified and stolen credit cards. Unit 42 further states that although one of the largest unpaid balances they uncovered on the fake accounts was $190, other accounts could have run up much larger bills.
“…we suspect the unpaid balances in other fake accounts and cloud services used by the actors could have been much larger due to the scale and breadth of the mining operation,” stated the report.
Creating the fake accounts
Unit 42’s report states that at the peak of the operation in November 2022, Automated Libra had created over 130,000 fake Github and Heroku accounts. Assuming that the accounts ran up an average of $100 in unpaid bills, the scheme cost Microsoft and Salesforce over $13 million in resources.
Microsoft-owned Github and Salesforce-owned Heroku are cloud platforms that enable developers to build, run, and operate applications entirely in the cloud, in this instance, crypto mining applications.
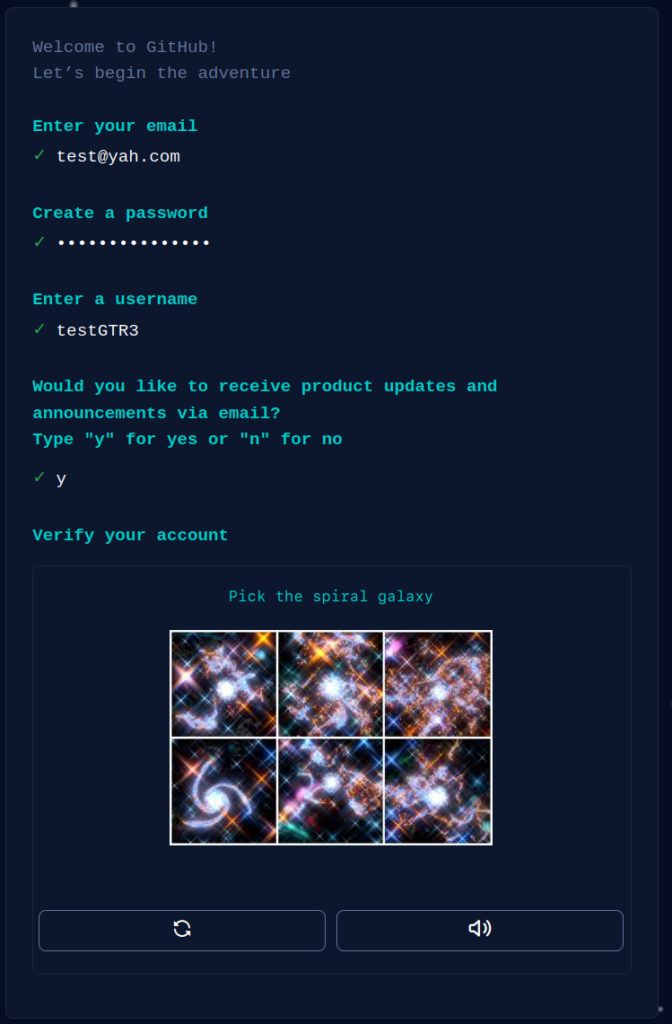
To create the accounts, the group used xdotool, a tool used to automatically generate keyboard and mouse inputs, to populate the Github account creation tool.
To complete the account creation process which requires correctly identifying a “CAPTCHA” image, the group employed ImageMagick tool kit, used to convert, edit and compose digital photos.
Through the tool, the hackers were able to correctly identify CAPTCHA images, allowing them to automatically complete the account creation process and proceed with the “freejacking” and “play and run” tactics.
According to Unit42, after mining the cryptocurrencies, Automated Libra also proceeded to automate the process of trading the collected cryptocurrencies across several crypto trading platforms including CRATEX ExchangeMarket, crex24, and Luno.
“Unit 42 researchers identified more than 40 individual crypto wallets and seven different cryptocurrencies or tokens being used within the PurpleUrchin operation,” the report adds.
Speaking to MyBroadband, Christo de wit, Luno country manager, stated that the exchange has not been contacted by any victims from the scheme and added that they would be able to identify the perpetrators behind the wallets should law enforcement require them to.
“Yes, with our KYC processes, we are able to provide relevant information to law enforcement agencies who request it while investigating this type of incident…Our FinCrime team also actively monitors transactions in accordance with regulations.” De Wit stated.
Over the last two years, South Africa has experienced its fair share of crypto scams. Last year, the US Commodities Futures Trading Commission (CFTC) charged South African resident Cornelius Johannes Steynberg in a bitcoin fraud scheme case totalling $1.7 billion.
In October last year, the National Consumer Commission (NCC) also announced that 4,000 South Africans had lost R112 million ($6.1 million) in a bitcoin mining pyramid scheme called Obelisk.