On the night of July 13, 2023, staff of Globacom—the Nigerian telecoms company that disrupted the industry in 2003 with ”per second” billing—could not access their emails or use work applications. Employees on the night shift didn’t panic because these glitches had become a pattern for at least two weeks. They spent the time talking, unaware this wasn’t another routine glitch.
The July 13 disruption was the beginning of a major cyber attack that left Globacom’s staff unable to do any work. The scale of the disruption was impossible to ignore.
Emails could not be sent or received, and vital work applications were inaccessible, leaving employees across multiple departments unable to get work done, said nine Globacom employees who asked not to be named.

The customer service team was the first to feel the heat.
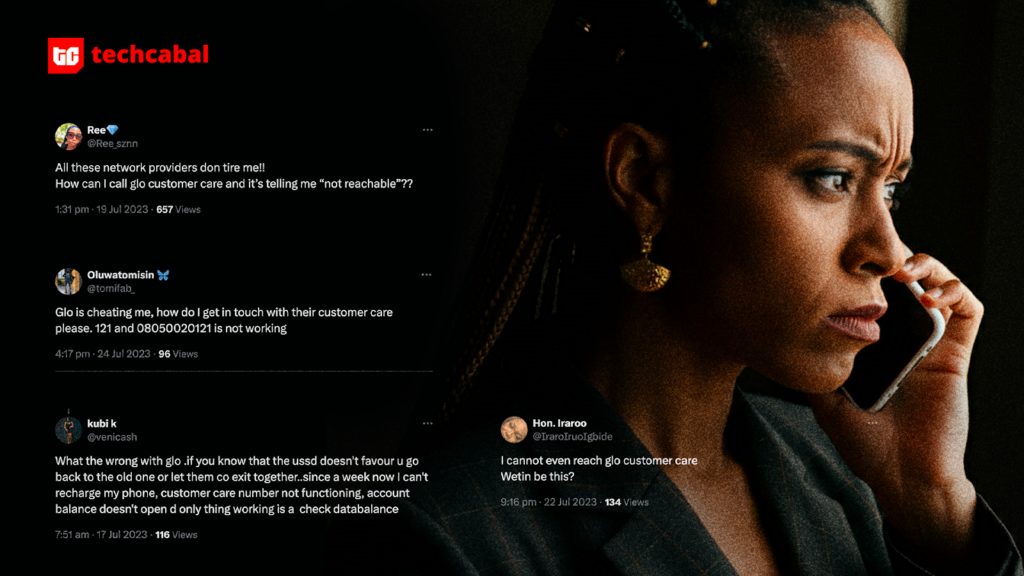
“Calls from customers were either not coming through or were being dropped,” said one person with direct knowledge of the matter. “We could not interact with customers.” Six Globacom employees confirmed customers could not call or email customer support for at least three weeks.
One user posted on X on July 16, “I’m unable to reach Glo through emails, calls, or customer service numbers. The answer is always, ‘invalid number, or your call cannot be completed.”
Internally, messaging tools like Microsoft Teams went down, severing communications between Globacom’s teams. The Human Resource Management Information System (HRMIS) was unreachable, halting basic administrative functions like leave requests, overtime logs, and payroll processing.
“We were coming to the office every day to sit around,” said an employee, describing work weeks with no updates from leadership or timeline for when systems would be restored.
The worst news came later: according to three people familiar with the incident, hackers also accessed customer data.
Conversations with over 30 people who asked not to be named discussing a sensitive company matter, revealed a picture of hackers likely gaining access to Globacom’s Domain Name System (DNS) in mid-2023.
The Nigerian Communications Commission (NCC) and the National Information Technology Development Agency (NITDA) both confirmed the attack on Globacom but did not share specifics.
According to a cybersecurity expert who requested anonymity, the attack on Globacom had been weeks in the making. The intermittent outages Globacom experienced leading up to the July 13 attack weren’t technical glitches–they were tests.
The method of attack suggested a Domain Name System (DNS) hijack–a type of attack that redirects traffic from legitimate websites to malicious ones. In Globacom’s case, according to the expert, the hackers likely infiltrated their DNS, effectively gaining control over email servers and the work applications connected to them.
“For four months, they didn’t know what happened and still don’t know,” said one former Globacom executive who asked not to be named. “Any customer data that was exposed has not been recovered, so there are many customers whose data might be sitting in the hacker’s hands.”
According to the Nigeria Data Protection Act 2023, Globacom is required to notify the telecoms regulator, the Nigerian Communications Commission (NCC), “within 72 hours of becoming aware of a breach which is likely to result in a risk to the rights and freedoms of individuals.”
Globacom didn’t report it; the commission approached them instead.
“The attack was not reported by Globacom initially, but the Commission, through its Cybersecurity Emergency Response Teams (CERT), had monitored the impending attack and brought it up [with the company],” the NCC told TechCabal in a statement.
The Data Protection Act allows the Nigeria Data Protection Commission (NDPC) to impose penalties on companies that fail to comply, including a fine of up to ₦10,000,000 or 2% of the company’s gross revenue if it’s a data controller of major importance.
The NDPC did not respond to multiple requests for comments.
Hackers like those responsible for the attack on Globacom are motivated by financial gain and the opportunity to expose vulnerabilities in large organisations.
Four Globacom employees claimed the hackers demanded a ransom to restore access to the company’s systems. While the exact amount demanded remains unclear, Globacom did not pay.
Globacom has not responded to three requests for comments since TechCabal first reached out in September 2023.
With no internal communications tools, teams began communicating on Whatsapp, which continued until early 2024, six people with knowledge of the situation said. TechCabal saw several of those internal company messages.
When TechCabal contacted three senior managers in September 2023 and requested their email addresses, two asked to speak on WhatsApp. The third person said they had “technical issues” with their email.
“Usually, my account manager verifies my transactions via email for record purposes.” said one enterprise partner who has worked with Globacom for three years said.
“In July 2023, my account manager said Globacom was having issues, and my transactions were verified on Whatsapp; I couldn’t reach my account manager through email for a month.”
As the company continued to be locked out of its email, it moved to webmail, two people with direct knowledge of the situation said.
The cyber attack on Globacom wasn’t an isolated incident–it’s part of a growing trend across Africa, where companies and institutions face unprecedented attacks.
According to recent data from Check Point, African companies now face an average of 3,370 cyber attacks per week, the highest in the world. The report also showed a 74% increase in cyber attacks worldwide, showing that these attacks have become more sophisticated.
In August 2023, another Telco giant, MTN Nigeria, experienced a DDoS attack. The NCC told TechCabal in a statement that “MTN systems proved to be robust as customer-facing services and customer data was not compromised as a result of the incident; hence, there was no need for the Commission to intervene.”
According to Wikipedia, a Denial of Service (DoS) or DDoS attack is like a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, disrupting trade and losing the business money.

MTN Nigeria did not respond to multiple requests for comments.
The hacker group Anonymous Sudan claimed responsibility on its Telegram channel for the cyberattack on MTN. Given the timing between the MTN attack and the Globacom breach, it was natural to question whether Anonymous Sudan was behind the Globacom assault.
But when TechCabal asked Anonymous Sudan about the Globacom attack, they denied any involvement.
One cybersecurity expert claimed that companies are susceptible to these attacks because they focus narrowly on preventing external threats. Internal mistakes often allow attackers to get in.
According to NITDA, the human factor is the biggest weakness in cyberattacks. However, the agency is clear that not reporting or sharing proves greater harm.
“Most of the organisations cover up when attacks happen, but it’s not good for the industry,” NITDA said, highlighting how fear of reputational damage often drives secrecy.
Over a year after the attacks first began, Globacom remains silent.
Despite multiple requests for comments, the company has yet to offer a clear explanation of what happened, how they responded, or how they intend to protect their customers going forward.
The real cost of this breach remains uncertain. Sensitive customer data could still be in the hands of cybercriminals. The ransom rumours have yet to be addressed. And the company’s reluctance to admit the full extent of the damage only raises more questions.
As cyber-attacks become more sophisticated, companies like Globacom will face increasing scrutiny—not just for the strength of their defences but for their willingness to be transparent when those defences fail. In the battle between secrecy and accountability, one thing is clear: silence only deepens the crisis.



















