Written by: Ayoola Afolabi
Drawing on my experience within the scams and fraud-prevention team of a leading UK bank, I have seen first-hand how technology, governance, and human insight converge to combat complex financial crime. Nigeria’s rapidly expanding digital-payments landscape now faces similar pressures: rising transaction volumes, sophisticated threat actors, and a fragmented detection architecture. Yet these challenges also present an opportunity, which is to engineer a smarter, data-driven, and collaborative fraud-defence ecosystem tailored to Nigeria’s financial reality.
1.From reactive defence to data-driven engineering
Fraud detection in many Nigerian institutions remains largely reactive. Rule-based systems monitor transactional thresholds, while analysts manually investigate alerts. These frameworks are effective for known typologies but fail against adaptive fraud patterns that mutate faster than static rules can adjust.
A mature ecosystem treats fraud detection as a data-engineering discipline—not a compliance obligation. This shift involves three engineering principles:
1. Data observability across customer, device, and transactional layers.
2. Model adaptability through continuous retraining and drift detection.
3. Operational feedback loops linking human analyst insights directly into model pipelines.
Banks can operationalise this through a unified fraud-data platform built on streaming architectures (e.g., Apache Kafka or Pulsar). Each event—login, payment initiation, device change—is transformed into a structured data object enriched with contextual metadata. These objects feed near-real-time inference models hosted on cloud-native microservices, enabling sub- second scoring latency (<150 ms) without disrupting customer experience.
2. Behavioural biometrics: Implementing invisible authentication
Traditional authentication—passwords, PINs, OTPs—has reached diminishing returns. Behavioural biometrics introduces an invisible layer of defence by modelling how genuine users interact with devices.
In practice, financial institutions can integrate a behavioural-biometrics SDK within their mobile or web applications. The SDK collects micro-interaction signals (keystroke dynamics, gyroscopic data, swipe pressure) and transforms them into anonymised feature vectors.
A central model, trained using federated learning and differential privacy, allows local devices to contribute to model updates without transferring raw behavioural data—critical for NDPR and GDPR compliance. The resulting behavioural-score model assigns risk in real time. Anomalies trigger adaptive friction: secondary verification, delayed payment release, or AI-driven customer challenge flows.
Such systems reduce account-takeover fraud by up to 40 per cent in comparable UK deployments, while maintaining a frictionless user experience.
3. Graph analytics: Mapping the fraud genome
Fraud rarely occurs in isolation; it is a network phenomenon. Traditional SQL-based detection overlooks the relational context between accounts, merchants, and devices. Graph-analytics systems reveal these hidden linkages.
Implementation requires constructing an entity-resolution layer where disparate identifiers— account numbers, BVNs, device IDs, phone numbers—are mapped to graph nodes. Relationships (e.g., shares device, transfers funds to, registered on same IP) form edges.
A graph database (such as Neo4j or TigerGraph) enables algorithms like PageRank centrality or community detection to identify clusters indicative of mule networks or collusive merchants. Advanced use cases employ graph-neural networks (GNNs) that learn embeddings of nodes and edges, allowing the model to infer unseen relationships and predict fraudulent subgraphs dynamically.
Operationally, these insights feed into a real-time orchestration engine that prioritises investigation queues, enabling analysts to focus on high-connectivity anomalies rather than isolated alerts.
4. Federated learning and secure collaboration
One of Nigeria’s greatest structural challenges is data siloing. Each bank or fintech operates its own detection model, while fraudsters share intelligence freely. Federated learning (FL) provides a privacy-preserving path to collaborative model training.
Under FL, each participating institution trains a local model on its internal dataset. A central aggregator—managed by a neutral authority such as NIBSS or the Central Bank of Nigeria— receives encrypted model weights rather than data. The aggregator performs secure parameter aggregation (e.g., using homomorphic encryption or differential privacy noise injection) and distributes updated global weights back to participants.
This approach ensures that model intelligence improves collectively without breaching data- sovereignty laws. A pilot across three major banks could focus on card-not-present fraud, comparing uplift metrics such as AUC (area under curve) and recall improvements versus isolated models. Success would justify national rollout under a regulated framework.
5. Real-time orchestration and case-management pipelines
Even the best detection algorithms lose value without efficient orchestration. Nigerian banks can deploy event-driven orchestration platforms that unify detection, decisioning, and case management.
A reference architecture includes:
– Stream ingestion layer capturing transaction events and contextual metadata.
– Inference microservices performing model scoring and feature-store lookups.
– Decision engine executing policy logic (e.g., block, hold, or step-up verification).
– Case-management API integrating with CRM or ticketing systems for analyst review.
Such orchestration enables closed-loop learning: analyst feedback (true/false positives) is streamed back to the model-training environment, improving accuracy over time. Modern banks can implement this with open-source toolchains—Kafka + Flink + Feast + MLflow—or commercial fraud-orchestration suites configured for local compliance.
6. Smart numbers: A shared, practical defence layer
Many Nigerian scams originate via telephone numbers used for SIM-swap attacks, social- engineering calls, or mule recruitment. Establishing a Smart Numbers registry offers a lightweight but high-impact shared-intelligence mechanism.
System design:
– Each participating institution contributes hashed and salted phone numbers or device identifiers linked to confirmed fraudulent activity.
– A secure API gateway allows risk-scoring queries in near real time.
– Tiered access ensures only aggregated scores (e.g., low/medium/high risk) are returned, preserving user privacy.
Governance:
– Oversight by a joint committee of NIBSS, NCC, and participating banks.
– Data contribution validated via digital-signature verification to prevent poisoning.
– Independent audits and revocation protocols maintain trust.
This model mirrors the Shared Intelligence Hub concept deployed by UK Finance, adapted for
Nigeria’s telecom-integrated fraud vectors. Within six months of pilot adoption, participants
could benchmark reductions in authorised push-payment (APP) scams and SIM-swap incidents per 10,000 transactions.
7. Building a national fraud-intelligence layer
To institutionalise collaboration, Nigeria can engineer a National Fraud-Intelligence Layer
(NFIL)—a federated data-exchange fabric that connects banks, fintechs, and telecom operators.
Core components:
1. Secure Data Gateway: API mesh using OAuth 2.0 and zero-trust authentication to enable controlled data exchange.
2. Metadata Catalog: Schema registry ensuring semantic interoperability across institutions.
3. Anonymised Graph Repository: Aggregates cross-bank entity relationships using privacy- enhancing computation.
4. Analytics Sandbox: Regulated environment where approved analysts can run federated queries under strict logging and purpose limitation.
NFIL’s operational model would mirror the UK’s Economic Crime Data Strategy, aligning with NDPR principles. Governance frameworks should mandate data-minimisation, auditability, and ethical-AI oversight committees to manage algorithmic bias and explainability.
8. Measuring success: Engineering metrics that matter
Quantitative metrics transform fraud prevention from reactive firefighting to continuous improvement.
Institutions should track:
Precision & Recall: ≥ 0.85 / ≥ 0.70
Latency (ms): < 150 ms per transaction
False-Positive Rate: < 2 %
Model-Drift Index: < 10 % feature-distribution variance
Mean Time to Detect (MTTD): < 60 seconds
Fraud-Loss Ratio (FLR): < 0.05 % of total transaction value.
These indicators anchor fraud detection as a measurable engineering function, not an abstract risk domain.
9.The human intelligence layer
Technology amplifies—but never replaces—human judgement. Fraudsters exploit psychology as
much as system vulnerabilities.
Continuous training for analysts and contact-centre staff should incorporate behavioural-science modules: recognising linguistic red flags, urgency cues, and cognitive manipulation. AI-assisted case-management tools can surface explainable-AI narratives—why the model flagged a case— helping analysts make defensible, bias-aware decisions.
Cross-functional “fraud guilds,” combining data engineers, investigators, and UX designers, can run quarterly fraud retrospectives to identify feature gaps and user-journey weaknesses, mirroring DevSecOps culture in engineering teams.
10. Towards a collaborative future
The evolution of fraud mirrors the evolution of technology itself—decentralised, adaptive, and increasingly automated. To win smarter, Nigeria’s financial sector must evolve in kind.
By fusing behavioural intelligence, graph analytics, and federated learning within a shared- governance framework, the ecosystem can transition from siloed detection to predictive prevention. Initiatives like Smart Numbers and the National Fraud-Intelligence Layer embody a pragmatic path forward—scalable, privacy-preserving, and implementable today.
When banks begin to engineer fraud detection with the same rigour applied to payment innovation, every incident becomes not a setback but a learning vector. Trust—the most valuable currency of any digital economy—will then be protected not by chance, but by design.
Visual Appendices
Figure 1: Fraud Detection Data Pipeline
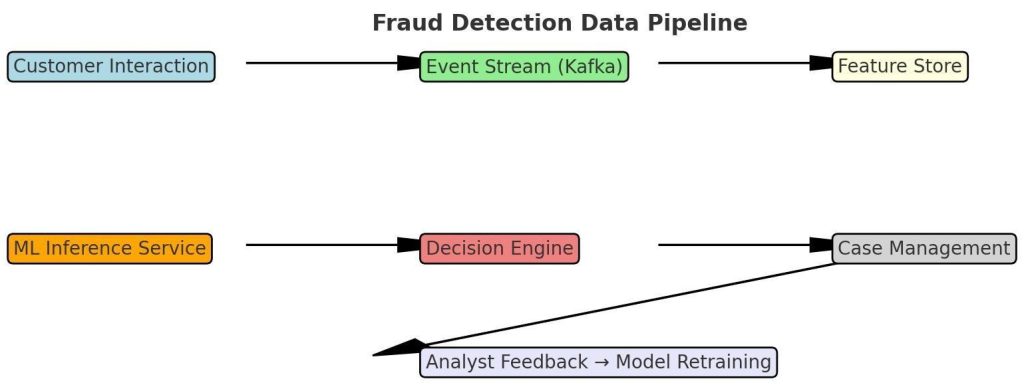
Figure 2: Federated Learning Architecture
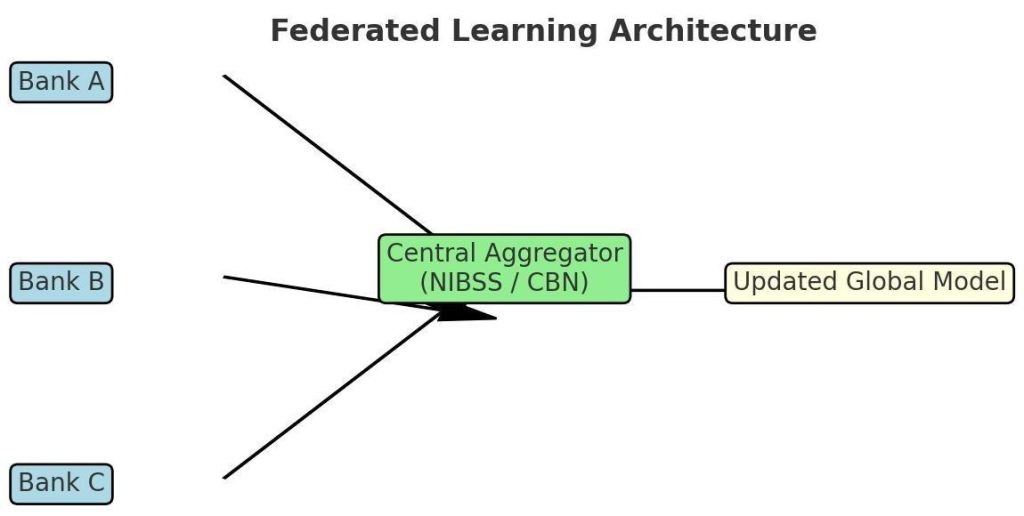
Figure 3: Smart Numbers System Overview
Smart Numbers System Overview
I Banks & Fintechs J Secure API Gateway Smart Numbers Registry
Governance: NIBSS + NCC Oversight
About the author
Ayoola Afolabi is a UK-based fraud-prevention and financial technology professional working at the intersection of data, risk intelligence and human judgement. Currently a Fraud and Change Professional at Barclays UK, he brings cross-market experience from Nigeria and the UK, with a focus on collaborative fraud-detection systems, smart data infrastructure and trust-building in financial services.















